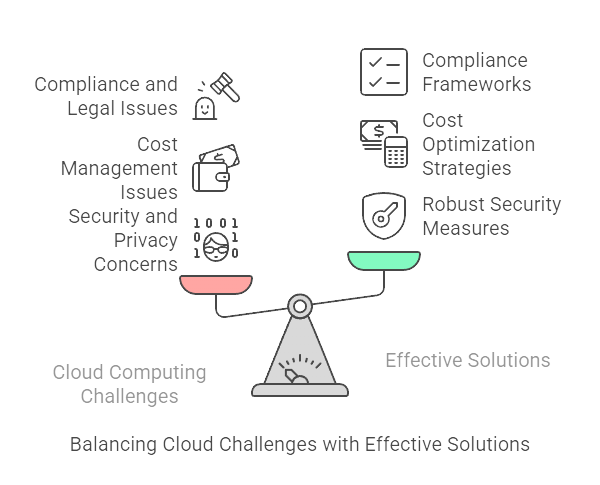
Summary: Cloud computing offers immense benefits but comes with challenges like security risks, cost management, and compliance issues. This blog highlights the most common hurdles and provides actionable strategies to overcome them, ensuring businesses can leverage cloud technology efficiently and securely for sustained growth and innovation.
Introduction
Cloud computing has revolutionized how businesses operate, offering scalable resources, flexibility, and cost savings. However, despite its advantages, organizations encounter several challenges when adopting or managing cloud services.
Understanding these challenges and how to address them is crucial for maximizing cloud benefits. Here’s an in-depth look at the most common challenges of cloud computing and effective methods to overcome them.
Key Takeaways
- Strong security protocols are essential to protect cloud data and privacy.
- Effective cost management prevents unexpected cloud expenses.
- Compliance requires continuous monitoring and governance in the cloud.
- Phased migration minimizes risks and ensures data integrity.
- Multi-cloud strategies reduce vendor lock-in and increase flexibility.
Challenges of Cloud Computing and Their Solutions
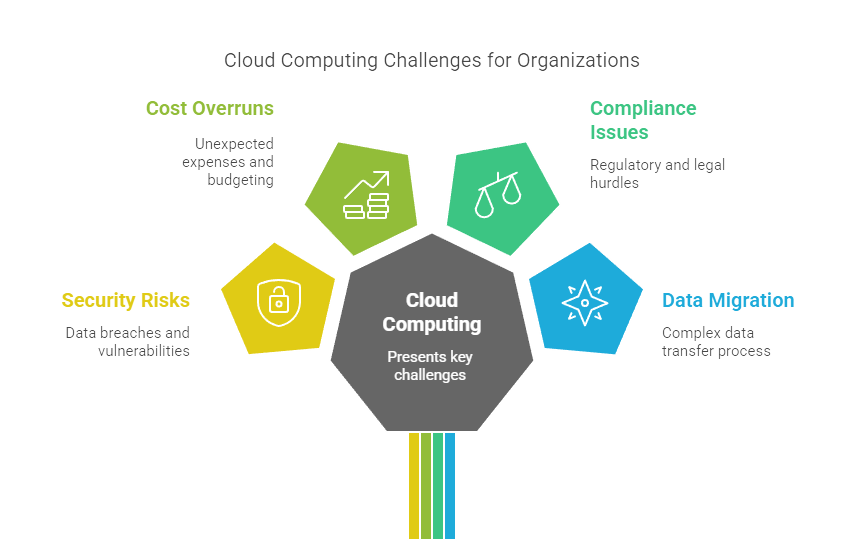
Cloud computing, while transformative, presents several key challenges such as security risks, cost overruns, compliance issues, and data migration complexities. Addressing these obstacles with effective solutions is essential for organizations to fully leverage cloud benefits, ensure operational efficiency, and maintain data integrity in an ever-evolving digital landscape.
Security and Privacy Concerns
Security and privacy are consistently ranked as the most significant concerns for organizations moving to the cloud. The risks include data breaches, unauthorized access, data leaks, and loss of sensitive information.
Cloud environments are attractive targets for cybercriminals due to the concentration of valuable data. Additionally, organizations often struggle with visibility and control over their data once it is hosted on third-party infrastructure.
Key Security Threats:
- Data Breaches: Unauthorized parties gaining access to confidential information.
- Account Hijacking: Attackers exploiting weak credentials or vulnerabilities.
- Insecure APIs: Poorly secured interfaces can expose data and services.
- Insider Threats: Malicious or careless employees causing data leaks.
- Shared Technology Vulnerabilities: Multi-tenant cloud environments can introduce risks if isolation fails.
Solution
Encryption
Encrypt all sensitive data both at rest and in transit. Use robust encryption algorithms and manage encryption keys securely, preferably with hardware security modules (HSMs) or key management services provided by the cloud vendor.
Multi-Factor Authentication (MFA) and Role-Based Access Control (RBAC)
Implement MFA to add an extra layer of security beyond passwords. RBAC ensures users only have access to the resources necessary for their roles, minimizing the risk of unauthorized access.
Regular Updates and Patch Management
Keep all cloud-based systems, applications, and dependencies up-to-date with the latest security patches. Many cloud providers offer automated patch management tools-leverage these to reduce vulnerabilities.
Security Audits and Penetration Testing
Schedule regular security assessments, including vulnerability scans and penetration tests. These help identify and address weaknesses before they can be exploited.
Cost Management and Optimization
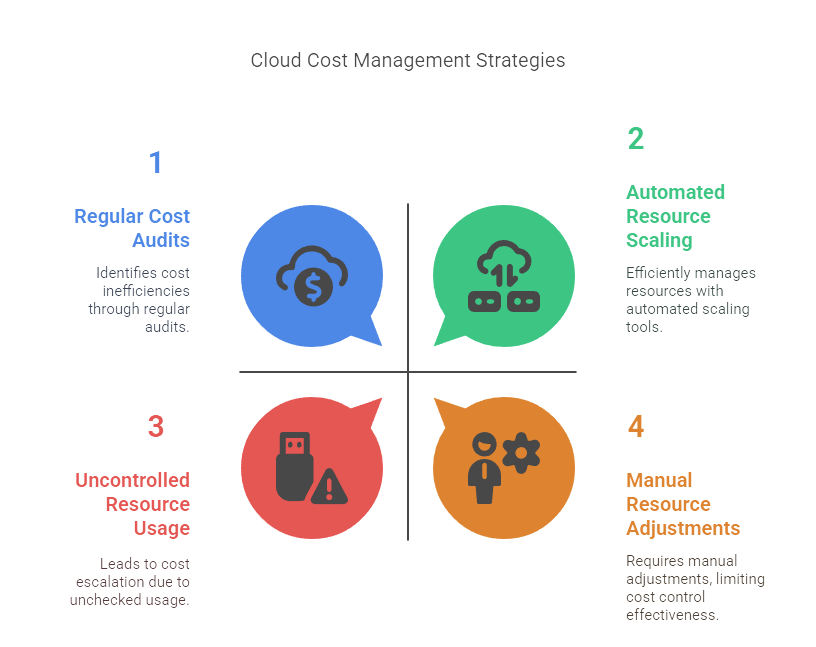
Cloud’s pay-as-you-go pricing model is flexible, but without proper oversight, costs can quickly escalate due to over-provisioned resources, unused services, or lack of visibility into spending.
Solution
Cloud Cost Management Tools
Utilize native tools like AWS Cost Explorer, Azure Cost Management, or Google Cloud Billing Reports to gain visibility into spending patterns and identify cost drivers.
Budgets and Alerts
Set up budgets and configure alerts to notify stakeholders when spending approaches predefined thresholds, preventing unexpected overruns.
Resource Optimization
Regularly review cloud usage to identify idle or underutilized resources. Rightsize virtual machines and storage, and terminate unnecessary instances.
Compliance and Legal Issues
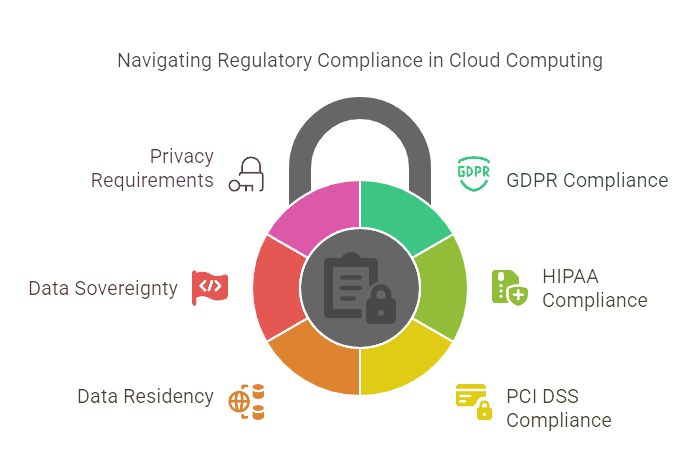
One of the key challenges of cloud computing is that cloud environments must comply with various regulations (GDPR, HIPAA, PCI DSS, etc.), which can be complex due to data residency, sovereignty, and privacy requirements.
Solution
Choose Compliant Providers
Select cloud vendors with certifications relevant to your industry and region, such as SOC 2, ISO 27001, or FedRAMP.
Data Classification and Governance
Implement policies to classify data based on sensitivity and apply appropriate controls. Use tools to enforce data governance and lifecycle management.
Audit Trails and Documentation
Enable logging and maintain comprehensive audit trails for all access and administrative actions. This supports compliance reporting and incident investigations.
Data Migration and Integration
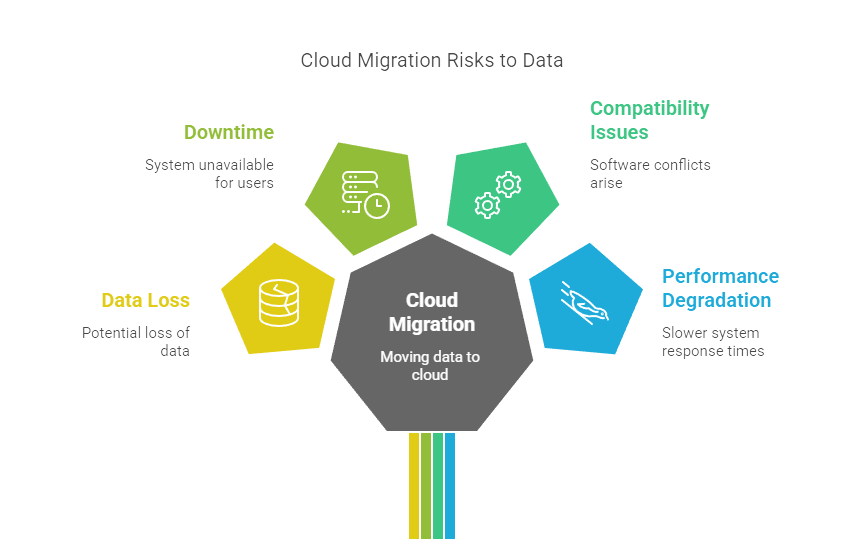
Migrating data and applications to the cloud can be complex, involving risks such as data loss, downtime, compatibility issues, and performance degradation.
Solution
Phased Migration Planning
Break down migration into manageable phases, starting with non-critical workloads. This reduces risk and allows for incremental learning and adjustment.
Cloud Migration Tools
Leverage provider-specific tools (e.g., AWS Migration Hub, Azure Migrate, Google Cloud Migrate) to automate and streamline the migration process.
Data Backup and Recovery
Back up all data before migration. Test recovery processes to ensure data integrity and availability in case of failures.
Vendor Lock-in
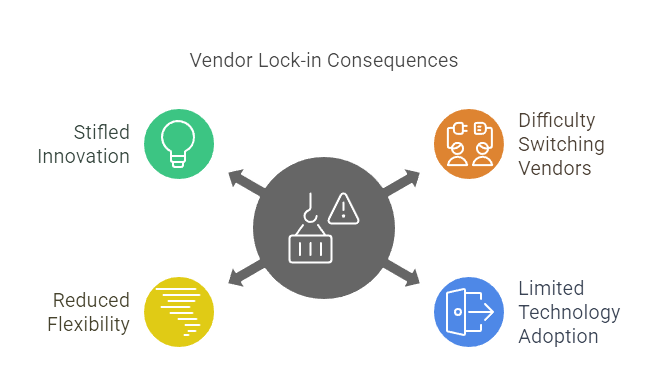
Over-reliance on a single cloud provider can make it difficult and costly to switch vendors or adopt new technologies, restricting flexibility and innovation.
Solution
Multi-Cloud and Hybrid Strategies
Distribute workloads across multiple cloud providers or combine public and private clouds to increase flexibility and reduce dependency.
Containerization and Orchestration
Use containers (Docker) and orchestration platforms (Kubernetes) to package applications and dependencies, enabling easy movement between environments.
Cloud-Agnostic Application Design
Build applications using open standards and avoid proprietary services where possible. Use abstraction layers to minimize dependency on specific vendor APIs.
Performance and Downtime
Cloud service outages and performance bottlenecks can disrupt business operations, leading to lost revenue and diminished customer trust.
Solution
Redundancy and High Availability
Deploy applications across multiple availability zones and regions to ensure resilience against localized failures.
Disaster Recovery Planning
Implement robust disaster recovery (DR) plans, including regular backups and failover procedures, to minimize downtime.
Continuous Monitoring
Use monitoring tools (e.g., AWS CloudWatch, Azure Monitor) to track performance metrics and receive real-time alerts for anomalies.
Lack of Skilled Personnel
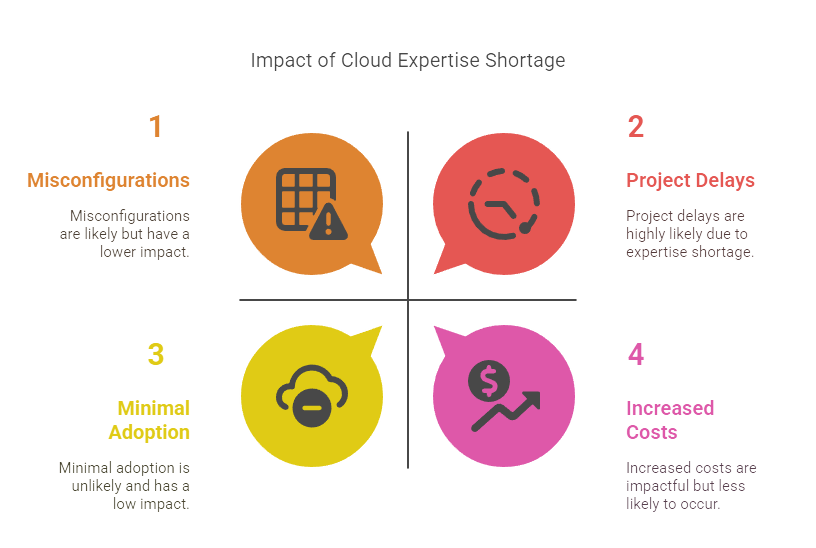
A shortage of professionals with cloud expertise can hinder cloud adoption, slow down projects, and increase the risk of misconfigurations.
Solution
Training and Certification
Invest in ongoing training and certification programs for IT staff (e.g., AWS Certified Solutions Architect, Azure Administrator Associate).
Managed Service Providers (MSPs)
Partner with MSPs or cloud consulting firms to access specialized skills and accelerate cloud adoption.
Internal Knowledge Sharing
Encourage knowledge sharing and mentorship within the organization to build a culture of continuous learning.
Conclusion
Challenges of cloud computing are real but manageable with the right strategies. By prioritizing security, cost control, compliance, and skilled personnel, organizations can unlock the full potential of the cloud. Embracing best practices and tools ensures a smooth, secure, and cost-effective cloud journey.
Frequently Asked Questions
What is the Biggest Challenge in Cloud Computing?
The biggest challenge is security, as cloud environments are vulnerable to data breaches and unauthorized access. Implementing robust encryption, access controls, and regular security audits helps mitigate these risks effectively.
How Can Businesses Control Cloud Costs?
Businesses can control costs by monitoring usage with cloud cost management tools, setting budgets, rightsizing resources, and leveraging reserved instances for predictable workloads, ensuring efficient spending.
What is Vendor Lock-in and How to Avoid It?
Vendor lock-in occurs when a business becomes dependent on a single cloud provider, limiting flexibility. Avoid it by adopting multi-cloud or hybrid strategies and using cloud-agnostic technologies like containers.